Why Identity-First is the New Perimeter
As cloud and hybrid environments blur traditional security borders, the Identity-First approach emerges as the foundation of modern cybersecurity. Both Zero Trust and Identity Fabric frameworks reinforce the principle: never trust, always verify for every user, device, and session fueled by federated identity and adaptive policies.
1. Zero Trust: From Concept to Reality
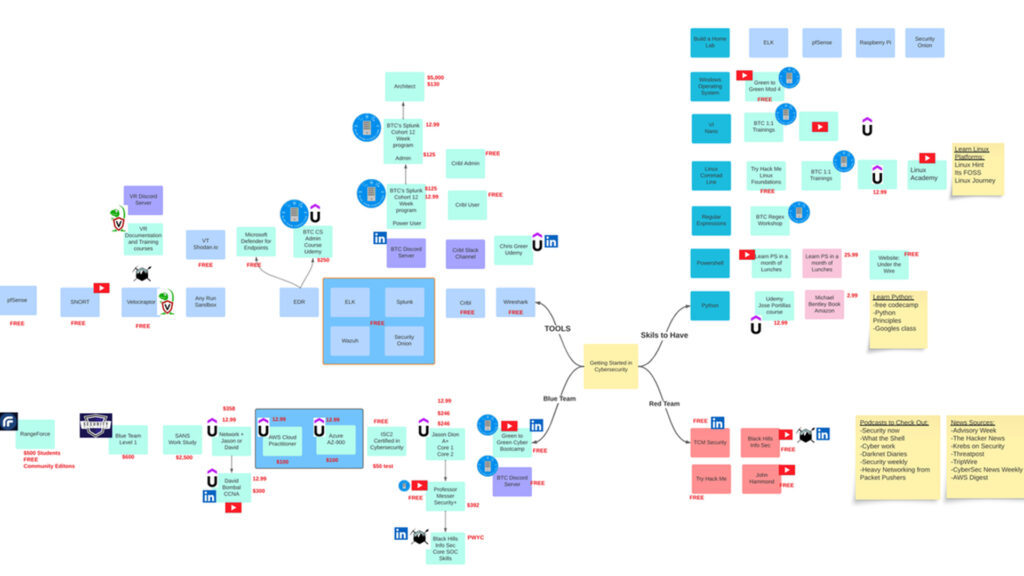
Origins & Core Principles
Coined in 2010 (Google’s BeyondCorp) and popularized by Forrester’s John Kindervag in 2014, Zero Trust rejects implicit trust even inside the network. It mandates:
- Verify every entity
- Enforce least privilege
- Continuously authenticate users/devices
- Context-based access policies
Reddit professionals emphasize this:
“Identity is a critical basis for zero trust…authentication is the first step, but authorization is the point”.
2. Federated Identity & Identity Fabrics
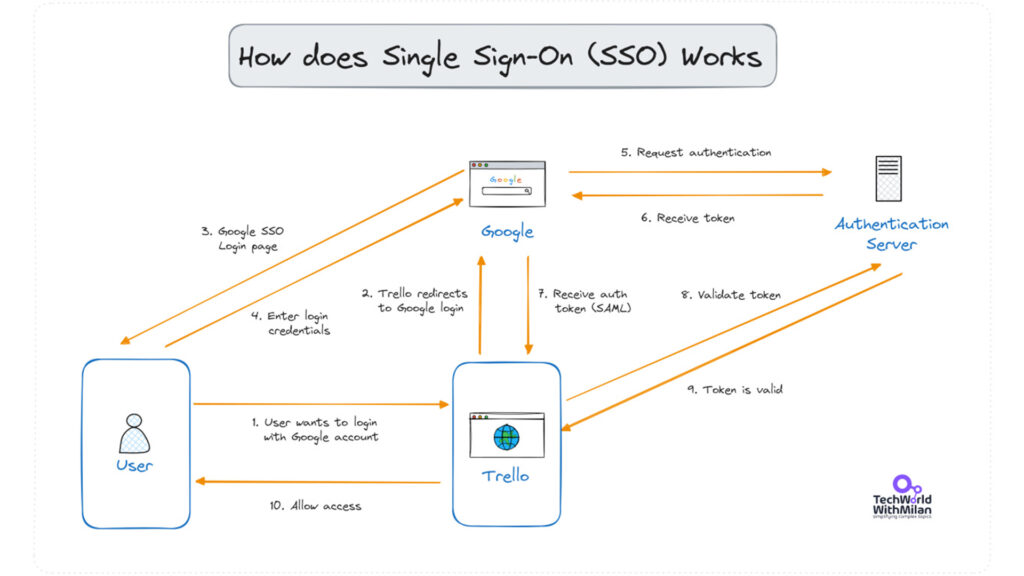
Source:-https://newsletter.techworld-with-milan.com/p/how-does-single-sign-on-sso-work
Federated Identity
Federated identity enables SSO across domains, trusting credentials issued by partner Identity Providers (IdPs), using SAML, OIDC, and OAuth. It reduces silos, improves UX, and enhances security.
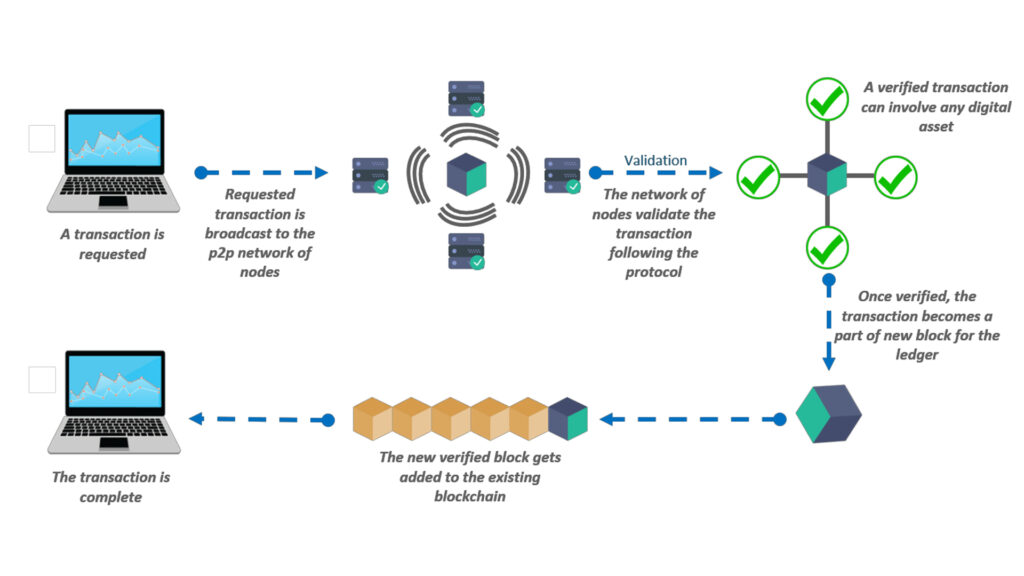
Identity Fabric
IBM’s Identity Fabric stitches multiple identity silos on-prem, cloud, third-party into a unified architecture. It supports multi-directory, vendor-agnostic interoperability (Okta, Microsoft, Ping), and modern protocols with no-code integration.
3. How IBM Drives Identity-First Architectures
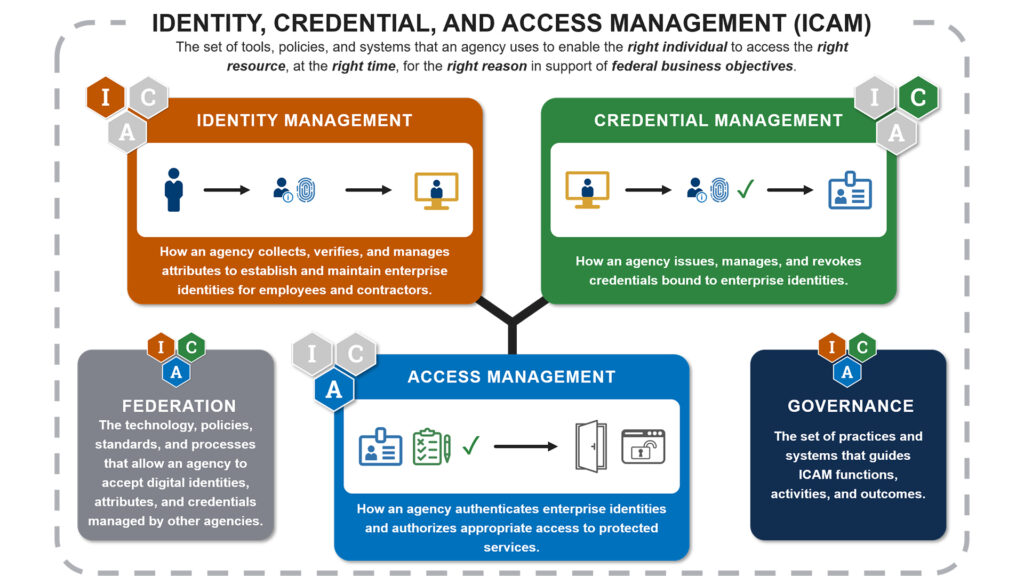
IBM Verify / Identity Fabric
IBM Verify offers a suite for workforce and consumer IAM:
- As a cloud-native, vendor-neutral fabric with centralized directories and no-code integrations.
- Adaptive, AI-powered access, with biometric risk scoring and real-time behavioral analytics.
Legacy integration via Application Gateway, bringing modern IAM to COBOL-era systems.
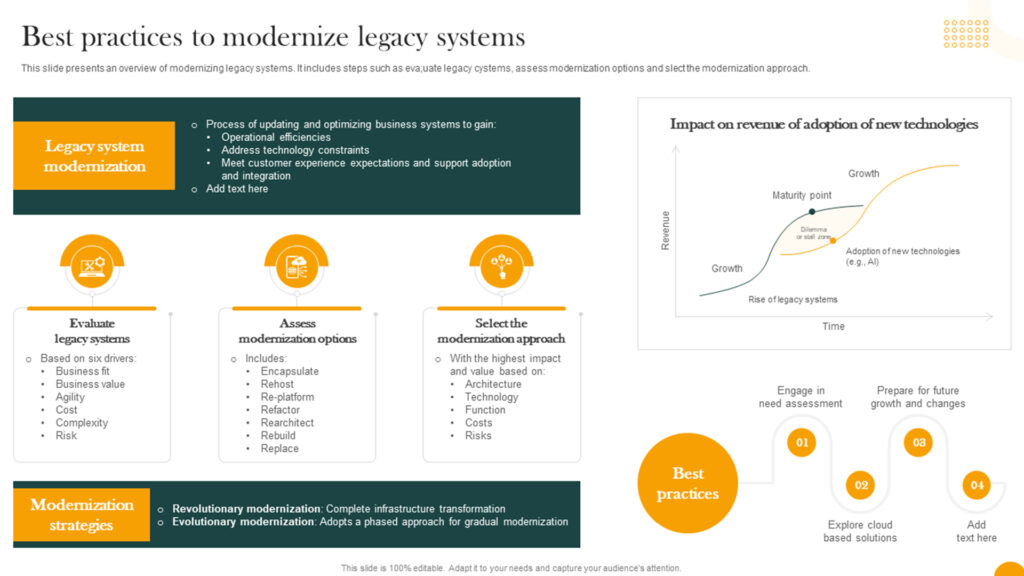
Scalable Zero Trust for internal/external identities with MFA options like QR, FIDO2.
IBM Case Study: Internal Transformation
IBM CIO consolidated two separate identity platforms into IBM Verify SaaS, supporting 27M+ identities and 35M+ logins per quarter. They deployed adaptive MFA (QR, FIDO2), bridging legacy systems with APIs. This showcases centralized, identity-first Zero Trust in action.

4. Academic Insights: Federated Zero Trust in Practice

Recent academic work strengthens this paradigm:
- “Federated Single Sign‑On and Zero Trust Co‑design…” outlines federated SSO integrated with runtime multi-factor, time-limited RBAC across AI/HPC infrastructures. Context-rich, time-bound identities reduce blast radius in sensitive environments.

- “Zero Trust Federation…” proposes context attribute providers sharing real-time device/user context across federated domains, vital for continuous access evaluation.
These models confirm: you can combine federated identity with Zero Trust, and still enforce continuous, context-aware verification.
5. Identity Fabrics as the Foundation of Zero Trust
Identity Fabrics makes Zero Trust practical and scalable by:
- Abstracting identity silos into a centralized, authoritative fabric.
- Enabling continuous verification using behavior analytics and AI.
- Enforcing least privilege & micro-segmentation via dynamic policies per identity and context.
- Governance & auditability, supporting compliance through traceability and access recertification.
6. Adoption Trends & Best Practices
- Phased implementation: start with high-risk applications—secure SSO and MFA, then expand identity context and governance.
- Hybrid integration: bridge legacy and cloud systems with identity fabrics—no rip-and-replace.
- AI-powered risk evaluation: continuously assess access requests using behavioral analytics and device context.
- Federated contexts: implement context attribute providers in federations, enabling Zero Trust across partners/institutions.
7. Measuring the Identity-First Success
Track metrics like:
- Reduction in identity-related breaches (60–65%)
- Authentication events are handled adaptively
- Time saved via SSO and federated login
- Contextual policy effectiveness and response latency
Championing the Identity-First Revolution
Identity Fabrics and federated Zero Trust mark a fundamental shift: identity itself becomes the security perimeter. IBM’s Verify platform, combined with federated identity research, offers practical, scalable architectures uniting continuous verification, least privilege, AI-backed context, and seamless interoperability.
By adopting identity-first frameworks, organizations can confidently secure hybrid, multi-cloud, and collaborative environments and stay ahead in the Identity-First Revolution.

