
Hey folks, Welcome to this Phishing Blog Part1.
As it began as a straightforward “hook, line, and sinker” fraud, phishing has evolved into something that is closer to a shark in a suit—it may appear smooth, but it bites hard! You don’t have to fall for the bait, which is good news. You may outsmart even the most cunning phishers by remaining vigilant, challenging anything that seems “off,” and staying up to date with the most recent cyber tactics.
What is Phishing?
Phishing is considered to be the most common cyber attack. It is the practice of sending fraudulent communication that appears from an authentic source but is sent to the target to steal sensitive information like credentials, payment card information, login information, etc. Phishing is usually done through emails where the attackers appear to be from reputable sources. By Phishing, an attacker can install malware into the Victim’s Machine.

Various Types of Phishing Attacks
1. Generic Phishing:
In Generic Phishing, Attackers send thousands of emails to thousands of victims hoping that someone will take the bait and get trapped.
2. Spear Phishing:
Spear Phishing is an attack on a specific individual or organization.

3. Whaling:
In Whaling Phishing, the Attacker targets Executives or High-Level personals like CEOs, COOs, Presidents etc.
4. Clone Phishing:
When an attacker spoofs or clones the official or legitimate mail but replaces the links and attachments with the malicious ones.
5. Pharming:
Pharming is also a type of Phishing but in Pharming the attacker sends a fraudulent website instead of emails or links. In pharming, victims do not have to click on the links or attachments to be taken on the bogus site. The attacker can directly infect the victims’ machines or the website’s DNS server and redirect the victim to the bogus site even if the legitimate URL is typed.
There are many other types of phishing like Email Phishing, Vishing, Smishing, CEO Fraud(Business Email Compromise- BEC), Social Media Phishing, Search Engine Phishing, Pop-Up Phishing, Angler Phishing, Watering Hole Phishing, Evil Twin Phishing, Malvertising etc.

How does Phishing Work?
Phishing is a dubious cyberattack when attackers replicate trustworthy entities in an attempt to mislead victims into revealing personal information, such as passwords or bank details.
These assaults frequently take the shape of false emails, messages, or websites that appear to be authentic. Understanding how phishing works is critical for being secure online.
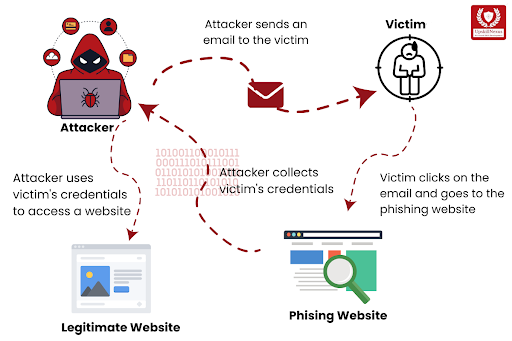
If you want to learn how phishing and other assaults work and how to defend against them, take our hacking course! Whether you’re an experienced computer user or just getting started, our course will educate you on how to efficiently navigate and secure the digital world.
What are the dangers of Phishing?
Sometimes an attacker can be satisfied by just stealing the Sensitive, Login or Bank details. But a few times phishing emails are sent to obtain the victim’s login information and other details for use in advance attacks against a specific Company. Advanced Persistent Attacks(APTs) and Ransomware Attacks are often started with Phishing Attacks.These attacks offer significant risks that go beyond individual victims, affecting larger social, economic, and political frameworks.
1. Social Dangers
- Phishing erodes trust in digital communications. Individuals become distrustful of emails, texts, and phone calls, resulting to reluctance to interact with legitimate institutions.
- Psychological Impact: Victims of phishing scams frequently experience worry, tension, or embarrassment, which undermines their trust in using online platforms.
- Widespread Misinformation: Spear-phishing attempts usually target social topics, creating false narratives and exacerbating societal divisions.
2. Economic dangers
- Financial Losses: Phishing causes billions of dollars in global losses each year. Attackers frequently empty bank accounts, carry out illicit transactions, and steal bitcoin.
- Corporate Espionage: Businesses targeted by phishing fear data breaches, intellectual property theft, and financial insecurity, particularly small and medium-sized enterprises (SMEs) that lack adequate cybersecurity defenses.
- Operational disruptions might include extended downtime, costly forensic investigations, and a loss of consumer trust.
3. Political dangers
- Election Interference: Phishing is used to infiltrate officials’ accounts, resulting in leaks or modification of critical information, threatening electoral integrity.
- National Security Risks: Phishing is used by cybercriminals and state-sponsored organizations to gain illegal access to government systems, which could compromise national security.
- Diplomatic Tensions: Cross-border phishing attempts can cause tensions between states since victims frequently regard them as acts of cyber warfare.
How to Identify a Phishing Email?
Distinguishing between legitimate and phishing emails can be difficult, but understanding what to look for can help you avoid falling victim. Here is a table below to show you how you can differentiate between a Phishing and Legitimate Email:
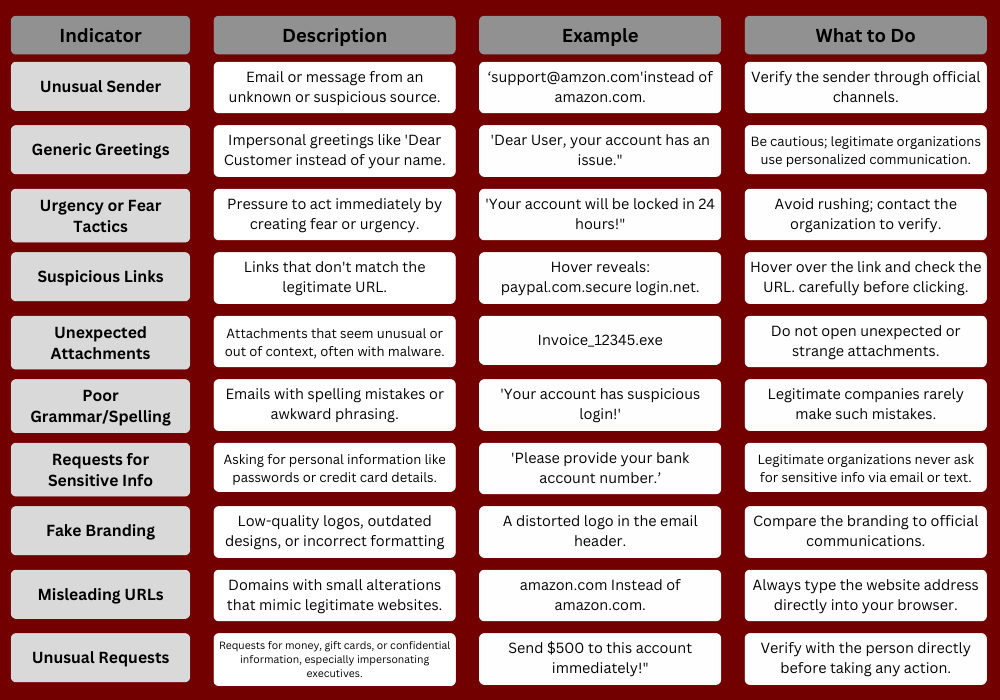
Red Flags For Everyone:
- Urgent tone: “Act immediately or your account will be suspended!”
- Generic greetings: If a corporation recognizes you, it will utilize your name.
- Poor grammar and spelling.
- Illegal links or attachments.
For Technical Reader: Dig Deeper
If you have technical skills, here are some more ways to investigate suspicious emails:
- Check the Email Headers: Check for disparities in the “From” and “Reply-To” boxes.
- Inspect Links: Hover over links to see their exact destination.
- Analyze Attachments: To open files safely, use tools like sandbox environments.
- Verify Domains: Use Whois or similar tools to authenticate the sender’s domain ownership.
Real Life Examples Of Phishing:
Example of a Fake Email (Phishing)
Subject: “URGENT: Your Account is Locked!”
Sender: support@paypa1.com
Body:
Dear Customer,
We noticed suspicious activity in your account. Please verify your identity within 24 hours to avoid suspension. Click here.
Red Flags:
- Misspelled domain (paypa1.com instead of paypal.com).
- Urgency and threat of account suspension.
- Generic greeting.
Example of a Real Email
Subject: “PayPal: Recent Account Update Confirmation”
Sender: service@paypal.com
Body:
Hi John,
You recently updated your account details. If this wasn’t you, please contact us immediately using the secure link below.
Green Flags:
- Personalized greeting.
- Professional tone.
- Legitimate link that matches PayPal’s official domain.
Protecting Yourself from Phishing Attacks.
Here’s how to reduce the likelihood of falling victim to phishing:
- Think Before You Click: Hover over links to confirm their destination.
- Enable Two-Factor Authentication (2FA): This adds a degree of security to your account.
- Use Security Software: Antivirus and anti-phishing extensions can add an added layer of protection.
- Educate yourself and others: Regularly upgrade your knowledge of phishing strategies.
- Verify suspicious messages: Contact the sender directly using official means.
Summary:
The truth is that, in the current digital era, cybersecurity is a superpower rather than merely a competence. And UpskillNexus is the ideal place to develop that ability. Our goal is straightforward: to transform curious students into cyber warriors. We’ll provide you the skills, strategies, and self-assurance you need to keep one step ahead of the hackers, whether they’re using ransomware, phishing, data breaches, or the next big thing in cyberspace.
Take control of the digital battlefield instead of merely avoiding the bait. By joining UpskillNexus, we can address all potential cyberattacks, not just phishing. After all, a solid education is the best defense, and we are here to help you become an expert in it.
