What if your firewall could learn, adapt, and fight back—automatically?

It’s 2:43 AM.
Your network is humming along, quiet and secure.
Suddenly, a new, unknown malware variant makes its way through the dark web backdoor.
Before a standard firewall even realizes it’s there, it’s already compromised.
Not this time.
This time, your firewall adapts in real time. It identifies the anomaly, inspects the threat, re-trains itself and blocks it—all within a fraction of a second.
Welcome to the era of dynamically retrainable firewalls, where next-generation network security meets machine learning.
Why Legacy Firewalls Are Failing Quickly

Legacy firewalls are rule-based—hundreds or thousands of rules. These are static, manually updated, and reactive rules. In today’s fast-paced threat landscape, this is a fatal weakness: Attackers evolve. Firewalls don’t.
Emerging threats like zero-day attacks, polymorphic viruses, and AI-driven phishing payloads don’t wait around for patching cycles. They evolve on the fly. And if your defenses can’t keep pace, your data is vulnerable.
Introducing Adaptive Firewalls

Adaptive firewalls, powered by machine learning (ML), do not simply rely on pre-set rules. They:
- Ongoingly examine traffic patterns
- Recognize subtle anomalies in real-time
- Learn from emerging threats across environments
- Retrain themselves on new threat intelligence autonomously
Think of them this way:
Traditional firewalls are bouncers. Adaptive firewalls are intel analysts, forensic specialists and first responders rolled into one.
So, What Makes Them "Dynamically Retrainable"?
Excellent question. Here’s the key concept

1. Continuous Learning
Instead of quarterly rule updates, retrainable firewalls are woven into ML pipelines that learn continuously from new data, like threat intel reports, endpoint logs, or traffic behavior in real time.
Example:
Palo Alto Networks’ Cortex XDR uses behavioral analytics and anomaly detection to adapt its defenses in real time, identifying threats signature-based tools miss.
2. Anomaly-Based Detection
Forget rigid rules. These firewalls use unsupervised learning algorithms to detect patterns of “normal” behavior. When a deviation is seen—e.g., an unusual spurt of encrypted traffic on a rarely used port—it’s flagged, quarantined, and analyzed in real-time.
3. Real-Time Retraining
With the aid of software like TensorFlow Extended (TFX) or MLflow, security devices can now dynamically—automatically—retrain their models. That is, the firewall responds nearly in real-time, battling unknown threats.
Adaptive in Action: A Scenario
Suppose that an attacker uses a novel C2 (command and control) protocol to extract data through an encrypted pipe.
A traditional firewall?
Missed it entirely.
An adaptive firewall?
- Notices traffic pattern is not consistent with known activity for that system
- Suspends the connection
- Queries a central threat intelligence hub
Flags the IP, updates its own threat model, and shares the information throughout the network
All in seconds.
The attack is stopped—not because the firewall observed the signature, but because it observed the behavior.
Real-World Applications and Case Studies
Cloudflare
Cloudflare’s Magic Firewall integrates adaptive security features to safeguard cloud infrastructure from DDoS and botnet attacks. It uses real-time telemetry and behavior-based filtering to protect edge and core environments concurrently.
Darktrace
Powered by AI and unsupervised learning, Darktrace’s Immune System replicates the defense system of the human body. Darktrace detects and neutralizes internal threats by continuously adjusting its definition of “self” for each network it protects.
Challenges to Consider
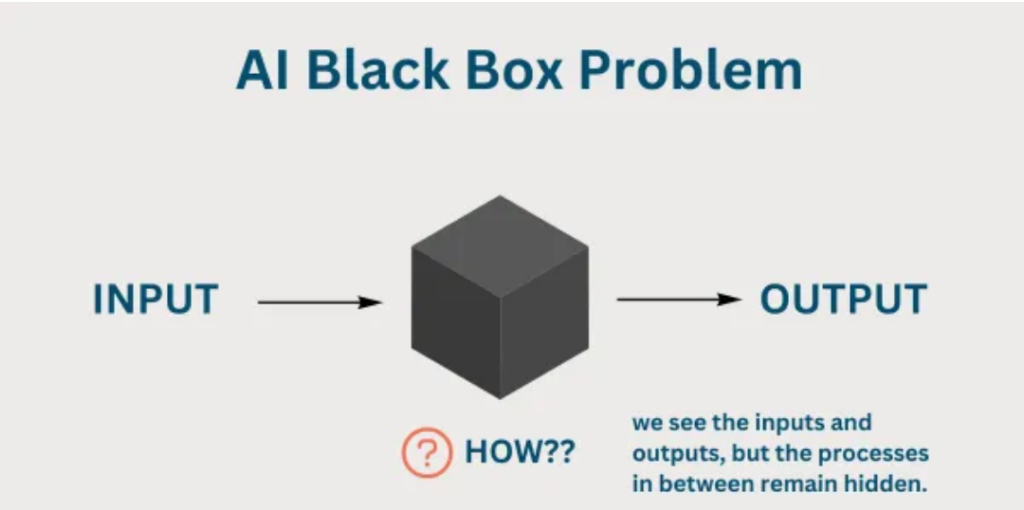
Adaptive firewalls look daunting—and they do—but they are not plug-and-play. Some things to keep in mind:
Quality of data matters: Trash in, trash out. Clean, correct traffic logs are required for ML models to learn.
Latency trade-offs: Inspection in real time and retraining add processing latency if designed with too much sloppiness.
Explainability: Black box adaptive systems. Security teams need tools to know why a decision was made (this is where Explainable AI fits in).
Security of the AI itself: ML models can be poisoned. Defense mechanisms need to have validation layers and input filtering to prevent manipulation.
- Implementation Tips: Start Smart
Not ready to redesign your infrastructure? Here's a roadmap to begin implementing adaptive firewalls incrementally:
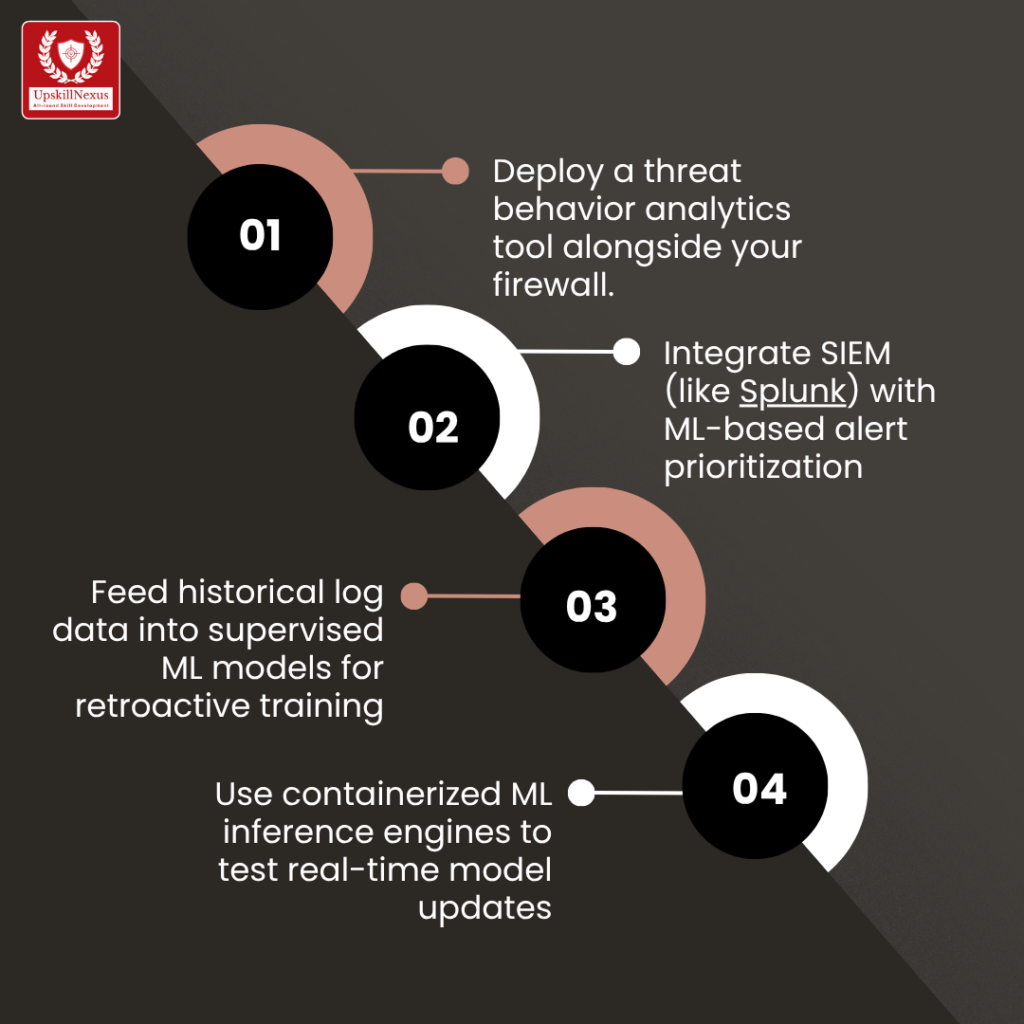
- Deploy a threat behavior analytics tool alongside your firewall
- Integrate SIEM (like Splunk)) with ML-based alert prioritization
- Feed historical log data into supervised ML models for retroactive training
- Use containerized ML inference engines to test real-time model updates
The Future: Predictive Defense Systems

In the next five years, the conversation will move from reaction to prediction.
We’ll see AI agents that collaborate across networks to flag global threats. Federated learning models that preserve privacy while sharing intelligence. Fully autonomous security pipelines, from detection to mitigation
And at the center of it all? Firewalls that learn. Firewalls that adapt. Firewalls that fight back.
Final Word
Cyber threats aren’t waiting. They’re mutating, evading, changing—always.
It’s time your firewall did the same thing.
Whether you’re running at the enterprise level or building next-generation cloud platforms, dynamically retrainable firewalls offer an active defense in a world of uncertainty.
If you want to keep learning about Firewalls and how to safeguard yourself, join UpskillNexus.

